Managing AD Cached Credentials and Okta Self-Service
For AD admins, managing remote workstations has become a neverending challenge.
Adopting Okta made things easier, but sometimes, quality-of-life features, such as AD password self-service, come with the cost of lacking native ways to verify credentials between a domain controller, the identity store (Okta), and the actual workstation.
So in this article, you will learn how to improve that a little.
Use Case Requirements
- An Okta tenant using AD Delegated Authentication
- A VPN where people log in using Okta
- Two available Workflows
- Connectivity and a service account for calling mail service APIs (depending on what your company is using)
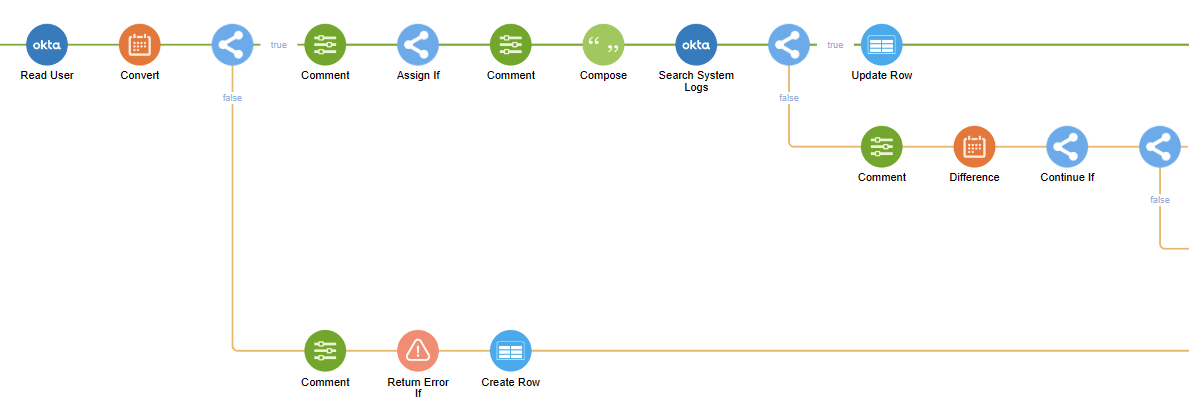
What does it do?
It checks if any user has changed their AD password through Okta Self-service. Then, every 24 hours it checks if the user logged in to the VPN, and if they didn't, it sends an email remind with instructions (e.g. "please connect to the VPN and perform a domain logon on your computer"), after 5 attempts if the user still didn't access the VPN, it will send a notification to your IT for manual intervention.
- It runs a scheduled Workflows trigger that checks for all the successful AD password reset events performed through Okta over a specified amount of days.
- It streams the records (from newest to latest) to a helper workflow.
- The helper flow then does all the magic of verifying timestamps, sending reminders, and keeping track of user activity to determine if subsequent reminders have to be sent or if to send a notification to your IT distribution list if the user ignores the request.
Download
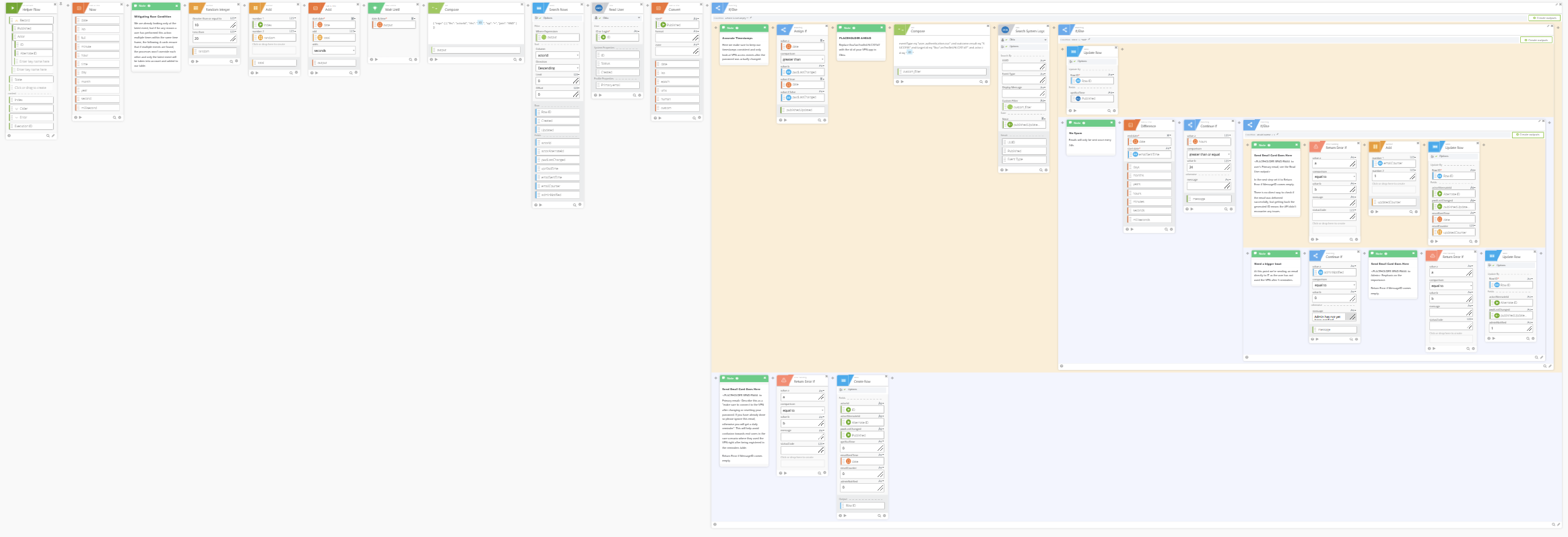
You will find Notes throughout the workflow explaining various steps.
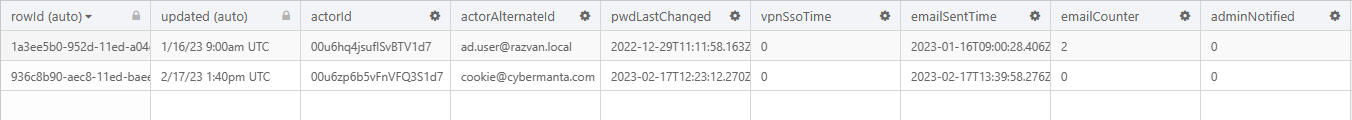
Make sure to import the table as well.
Make sure to hit Save on every If/Else block to make the workflow "unfold."
Limitations
There is no easy way to detect between an Okta delegated login event and an actual workstation login. Both activities update even the ms-DS-Last-Successful-Interactive-Logon-Time, so we can't track anything from Okta's side.
For the cached credentials to be updated, the user has to use them and not only be connected to the VPN. I recommend running a background script that automatically connects workstations to the VPN once the cached credentials are older than 10 days.
Notes
- How to Import the flows (make sure you import the helper first so you can easily assign it when you import the trigger):

Note that email connectors and email cards are not included. Those are simple to add; check out the connectors for Gmail and Office 365 Mail.
Questions or feedback?
Next
I will post two follow-up articles covering scenarios where the environment is hybrid and Azure AD comes into play, and another one where we can leverage MDM to secure the endpoint further and enforce up-to-date credentials.



